- Design features Version changes
- Internal structure SubBytes ShiftColumns MixRows AddRoundKey
- Whirlpool hashes
- Implementations
- Adoption
- See also
- References
- External links
|name = Whirlpool
|image =
|caption =
|designers = Vincent Rijmen, Paulo S. L. M. Barreto
|publish date = 2000, 2001, 2003
|series =
|derived from = Square, AES
|derived to =
|related to =
|certification = NESSIE
|digest size = 512 bits
|key size =
|security claim = Large hashsum size
|block size =
|state size =
|structure = Miyaguchi-Preneel
|rounds = 10
|cryptanalysis = In 2009, a rebound attack was announced that presents full collisions against 4.5 rounds of Whirlpool in 2120 operations, semi-free-start collisions against 5.5 rounds in 2120 time and semi-free-start near-collisions against 7.5 rounds in 2128 time.[1]
}}
In computer science and cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption Standard) and Paulo S. L. M. Barreto, who first described it in 2000.
The hash has been recommended by the NESSIE project. It has also been adopted by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) as part of the joint ISO/IEC 10118-3 international standard.
Design features
Whirlpool is a hash designed after the Square block cipher, and is considered to be in that family of block cipher functions.
Whirlpool is a Miyaguchi-Preneel construction based on a substantially modified Advanced Encryption Standard (AES).
Whirlpool takes a message of any length less than 2256 bits and returns a 512-bit message digest.[3]
The authors have declared that
"WHIRLPOOL is not (and will never be) patented. It may be used free of charge for any purpose."[2]
Version changes
The original Whirlpool will be called Whirlpool-0, the first revision of Whirlpool will be called Whirlpool-T and the latest version will be called Whirlpool in the following test vectors.
- In the first revision in 2001, the S-box was changed from a randomly generated one with good cryptographic properties to one which has better cryptographic properties and is easier to implement in hardware.
- In the second revision (2003), a flaw in the diffusion matrix was found that lowered the estimated security of the algorithm below its potential.[4] Changing the 8x8 rotating matrix constants from (1, 1, 3, 1, 5, 8, 9, 5) to (1, 1, 4, 1, 8, 5, 2, 9) solved this issue.
Internal structure
The Whirlpool hash function is a Merkle–Damgård construction based on an AES-like block cipher W in Miyaguchi–Preneel mode.[2]
The block cipher W consists of an 8×8 state matrix  of bytes, for a total of 512 bits.
of bytes, for a total of 512 bits.
The encryption process consists of updating the state with four round functions over 10 rounds. The four round functions are SubBytes (SB), ShiftColumns (SC), MixRows (MR) and AddRoundKey (AK). During each round the new state is computed as
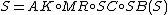 .
.
SubBytes
The SubBytes operation applies a non-linear permutation (the S-box) to each byte of the state independently. The 8-bit S-box is composed of 3 smaller 4-bit S-boxes.
ShiftColumns
The ShiftColumns operation cyclically shifts each byte in each column of the state. Column j has its bytes shifted downwards by j positions.
MixRows
The MixRows operation is a right-multiplication of each row by an 8×8 matrix over 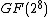 . The matrix is chosen such that the branch number (an important property when looking at resistance to differential cryptanalysis) is 9, which is maximal.
. The matrix is chosen such that the branch number (an important property when looking at resistance to differential cryptanalysis) is 9, which is maximal.
AddRoundKey
The AddRoundKey operation uses bitwise xor to add a key calculated by the key schedule to the current state. The key schedule is identical to the encryption itself, except the AddRoundKey function is replaced by an AddRoundConstant function that adds a predetermined constant in each round.
Whirlpool hashes
The Whirlpool algorithm has undergone two revisions since its original 2000 specification.
People incorporating Whirlpool will most likely use the most recent revision of Whirlpool; while there are no known security weaknesses in earlier versions of Whirlpool, the most recent revision has better hardware implementation efficiency characteristics, and is also likely to be more secure. As mentioned earlier, it is also the version adopted in the ISO/IEC 10118-3 international standard.
The 512-bit (64-byte) Whirlpool hashes (also termed message digests) are typically represented as 128-digit hexadecimal numbers.
The following demonstrates a 43-byte ASCII input (not including quotes) and the corresponding Whirlpool hashes:
| Version | Input String | Computed Hash |
|---|---|---|
| Whirlpool-0 | "The quick brown fox jumps over the lazy dog"4F8F5CB531E3D49A61CF417CD133792CCFA501FD8DA53EE368FED20E5FE0248C 3A0B64F98A6533CEE1DA614C3A8DDEC791FF05FEE6D971D57C1348320F4EB42D | |
| Whirlpool-T | "The quick brown fox jumps over the lazy dog"3CCF8252D8BBB258460D9AA999C06EE38E67CB546CFFCF48E91F700F6FC7C183 AC8CC3D3096DD30A35B01F4620A1E3A20D79CD5168544D9E1B7CDF49970E87F1 | |
| Whirlpool | "The quick brown fox jumps over the lazy dog"B97DE512E91E3828B40D2B0FDCE9CEB3C4A71F9BEA8D88E75C4FA854DF36725F D2B52EB6544EDCACD6F8BEDDFEA403CB55AE31F03AD62A5EF54E42EE82C3FB35 |
Even a small change in the message will (with an extremely high probability of 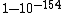 ) result in a different hash, which will usually look completely different just like two unrelated random numbers do. The following demonstrates the result of changing the previous input by a single letter (a single bit, even, in ASCII-compatible encodings), replacing d with e:
) result in a different hash, which will usually look completely different just like two unrelated random numbers do. The following demonstrates the result of changing the previous input by a single letter (a single bit, even, in ASCII-compatible encodings), replacing d with e:
| Version | Input String | Computed Hash |
|---|---|---|
| Whirlpool-0 | "The quick brown fox jumps over the lazy eog"228FBF76B2A93469D4B25929836A12B7D7F2A0803E43DABA0C7FC38BC11C8F2A 9416BBCF8AB8392EB2AB7BCB565A64AC50C26179164B26084A253CAF2E012676 | |
| Whirlpool-T | "The quick brown fox jumps over the lazy eog"C8C15D2A0E0DE6E6885E8A7D9B8A9139746DA299AD50158F5FA9EECDDEF744F9 1B8B83C617080D77CB4247B1E964C2959C507AB2DB0F1F3BF3E3B299CA00CAE3 | |
| Whirlpool | "The quick brown fox jumps over the lazy eog"C27BA124205F72E6847F3E19834F925CC666D0974167AF915BB462420ED40CC5 0900D85A1F923219D832357750492D5C143011A76988344C2635E69D06F2D38C |
The hash of a zero-length string is:
| Version | Input String | Computed Hash |
|---|---|---|
| Whirlpool-0 | ""B3E1AB6EAF640A34F784593F2074416ACCD3B8E62C620175FCA0997B1BA23473 39AA0D79E754C308209EA36811DFA40C1C32F1A2B9004725D987D3635165D3C8 | |
| Whirlpool-T | ""470F0409ABAA446E49667D4EBE12A14387CEDBD10DD17B8243CAD550A089DC0F EEA7AA40F6C2AAAB71C6EBD076E43C7CFCA0AD32567897DCB5969861049A0F5A | |
| Whirlpool | ""19FA61D75522A4669B44E39C1D2E1726C530232130D407F89AFEE0964997F7A7 3E83BE698B288FEBCF88E3E03C4F0757EA8964E59B63D93708B138CC42A66EB3 |
Implementations
The authors provide reference implementations of the Whirlpool algorithm, including a version written in C and a version written in Java.[2] These reference implementations have been released into the public domain.[2]
Adoption
Two of the first widely used mainstream cryptographic programs that started using Whirlpool were FreeOTFE, followed by TrueCrypt in 2005.{{Citation needed|date=February 2018}}
VeraCrypt (a fork of TrueCrypt) included Whirlpool (the final version) as one of its supported hash algorithms.[5]See also
- Digital timestamping
References
2. ^1 2 3 4 {{cite web| url=http://www.larc.usp.br/~pbarreto/WhirlpoolPage.html| title=The WHIRLPOOL Hash Function| author=Paulo S. L. M. Barreto| date=2008-11-25| archiveurl=https://web.archive.org/web/20171129084214/http://www.larc.usp.br/~pbarreto/WhirlpoolPage.html| archivedate=2017-11-29| deadurl=yes| accessdate=2018-08-09}}
3. ^{{cite journal| author1=Barreto, Paulo S. L. M.| author2=Rijmen, Vincent| lastauthoramp=yes| title=The WHIRLPOOL Hashing Function| date=2003-05-24| url=http://www.larc.usp.br/~pbarreto/whirlpool.zip| format=ZIP| archiveurl=https://web.archive.org/web/20171026140501/http://www.larc.usp.br/%7Epbarreto/whirlpool.zip| archivedate=2017-10-26| deadurl=yes| accessdate=2018-08-09}}
4. ^{{cite journal| title=On the diffusion matrix employed in the Whirlpool hashing function| author1=Kyoji, Shibutani| author2=Shirai, Taizo| lastauthoramp=yes| year=2003-03-11| url=https://www.cosic.esat.kuleuven.be/nessie/reports/phase2/whirlpool-20030311.pdf| format=PDF| accessdate=2018-08-09}}
5. ^{{cite web| url=https://www.veracrypt.fr/en/Whirlpool.html| title=Whirlpool| work=VeraCrypt Documentation| publisher=IDRIX| accessdate=2018-08-09}}
External links
- {{webarchive |url=https://web.archive.org/web/20171129084214/http://www.larc.usp.br/~pbarreto/WhirlpoolPage.html |date=2017-11-29 | title=The WHIRLPOOL Hash Function}}
- {{SourceForge|jacksum|Jacksum}}, a Java implementation of all three revisions of Whirlpool
- {{Github|jzelinskie/whirlpool}} – An open source Go implementation of the latest revision of Whirlpool
- [https://www.webcitation.org/65p0XVMV7?url=http://www.karljapetre.com/whirlpool/ A Matlab Implementation of the Whirlpool Hashing Function]
- RHash, an open source command-line tool, which can calculate and verify Whirlpool hash.
- [https://metacpan.org/pod/Digest::Whirlpool Perl Whirlpool] module at CPAN
- [https://rubygems.org/gems/digest-whirlpool Digest module] implementing the Whirlpool hashing algorithm in Ruby
- Ironclad a Common Lisp cryptography package containing a Whirlpool implementation
- [https://www.iso.org/standard/39876.html The ISO/IEC 10118-3:2004 standard]
- [https://www.cosic.esat.kuleuven.be/nessie/testvectors/hash/whirlpool/index.html Test vectors for the Whirlpool hash] from the NESSIE project
- Managed C# implementation
- 1929 Vermont Catamounts football season
- 1929 Vermont Catamounts football team
- 1929 Villanova Wildcats football
- 1929 Villanova Wildcats football season
- 1929 Villanova Wildcats football team
- 1929 Virginia Cavaliers football
- 1929 Virginia Cavaliers football season
- 1929 Virginia Cavaliers football team
- 1929 Virginia gubernatorial election
- 1929 Virginia Tech Hokies football team
- 1929 Volta a Catalunya
- 1929 VPI Gobblers football
- 1929 VPI Gobblers football season
- 1929 VPI Gobblers football team
- 1929 Wake Forest Demon Deacons football
- 1929 Wake Forest Demon Deacons football season
- 1929 Washington Huskies football
- 1929 Washington Huskies football season
- 1929 Washington State Cougars football
- 1929 Washington State Cougars football season
- 1929 Washington State Cougars football team
- 1929 Wellington City mayoral election
- 1929 Wellington mayoral election
- 1929 Western Maryland Green Terror football team
- 1929 Western Samoan general election