- The network
- The adversary
- The algebraic model Remark
- See also
- References
The Dolev–Yao model[1] is a formal model used to prove properties of interactive cryptographic protocols.[2][3]
The network
The network is represented by a set of abstract machines that can exchange messages.
These messages consist of formal terms. These terms reveal some of the internal structure of the messages, but some parts will hopefully remain opaque to the adversary.
The adversary
The adversary in this model can overhear, intercept, and synthesize any message and is only limited by the constraints of the cryptographic methods used. In other words: "the attacker carries the message."
This omnipotence has been very difficult to model and many threat models simplify it, as, for example, the attacker in ubiquitous computing.
The algebraic model
Cryptographic primitives are modeled by abstract operators. For example, asymmetric encryption for a user  is represented by the encryption function
is represented by the encryption function  and the decryption function
and the decryption function  . Their main properties are that their composition is the identity function (
. Their main properties are that their composition is the identity function ( ) and that an encrypted message
) and that an encrypted message  reveals nothing about
reveals nothing about 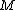 . Unlike in the real world, the adversary can neither manipulate the encryption's bit representation nor guess the key. The attacker may, however, re-use any messages that have been sent and therefore become known. The attacker can encrypt or decrypt these with any keys he knows, to forge subsequent messages.
. Unlike in the real world, the adversary can neither manipulate the encryption's bit representation nor guess the key. The attacker may, however, re-use any messages that have been sent and therefore become known. The attacker can encrypt or decrypt these with any keys he knows, to forge subsequent messages.
A protocol is modeled as a set of sequential runs, alternating between queries (sending a message over the network) and responses (obtaining a message from the network).
Remark
The symbolic nature of the Dolev–Yao model makes it more manageable than computational models and accessible to algebraic methods but potentially less realistic. However, both kinds of models for cryptographic protocols have been related.[4] Also, symbolic models are very well suited to show that a protocol is broken, rather than secure, under the given assumptions about the attackers capabilities.
See also
- Security
- Cryptographic protocol
References
2. ^{{Citation | last1 = Backes | first1 = Michael | last2 = Pfitzmann | first2 = Birgit | last3 = Waidner | first3 = Michael | title = Soundness Limits of Dolev-Yao Models | url = https://hal.archives-ouvertes.fr/docs/00/08/06/78/PDF/paper6.pdf | series = Workshop on Formal and Computational Cryptography (FCC'06), affiliated with ICALP'06 | year = 2006 }}
3. ^{{Citation | last1 = Chen | first1 = Quingfeng | last2 = Zhang | first2 = Chengqi | last3 = Zhang | first3 = Shichao | title = Secure Transaction Protocol Analysis: Models and Applications | url = https://books.google.com/?id=IMIuV_tUYfMC&printsec=frontcover&dq=secure+transaction+protocol+analysis+models+applications#v=onepage&q&f=false | series = Lecture Notes in Computer Science / Programming and Software Engineering | year = 2008 | isbn = 9783540850731 }}
4. ^{{Citation | contribution = A Computational Interpretation of Dolev-Yao Adversaries | citeseerx = 10.1.1.94.2941 | last1 = Herzog | first1 = Jonathan | year = 2005}}
- Ken Dedes
- Kendell Airlines
- Kender (Dragonlance)
- Kendermore
- Kendheraa
- Kendhikolhudhoo
- Kendhikolhudhoo (Noonu Atoll)
- Kendhoo
- Ken Dillen
- Kendleton
- Kendleton, Texas
- Kendleton, TX
- Kendo
- Ken Dodd
- Ken Doherty
- Ken Dolan
- Ken (doll)
- Ken doll
- Ken Done
- Ken Dorsey
- Kendo stick
- Ken Downing
- KendraPara
- Kendrapara district
- Kendra Slawinski