- Definition
- Applications
- Binary hash chains
- Hash chain vs. blockchain
- See also
- References
A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method to produce many one-time keys from a single key or password. For non-repudiation a hash function can be applied successively to additional pieces of data in order to record the chronology of data's existence.
Definition
A hash chain is a successive application of a cryptographic hash function  to a string
to a string  .
.
For example,
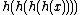
gives a hash chain of length 4, often denoted 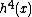
Applications
{{main article|S/KEY}}Lamport[1] suggested the use of hash chains as a password protection scheme in an insecure environment. A server which needs to provide authentication may store a hash chain rather than a plain text password and prevent theft of the password in transmission or theft from the server. For example, a server begins by storing 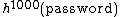 which is provided by the user. When the user wishes to authenticate, he supplies
which is provided by the user. When the user wishes to authenticate, he supplies 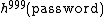 to the server. The server computes
to the server. The server computes 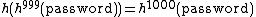 and verifies this matches the hash chain it has stored. It then stores
and verifies this matches the hash chain it has stored. It then stores 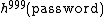 for the next time the user wishes to authenticate.
for the next time the user wishes to authenticate.
An eavesdropper seeing 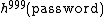 communicated to the server will be unable to re-transmit the same hash chain to the server for authentication since the server now expects
communicated to the server will be unable to re-transmit the same hash chain to the server for authentication since the server now expects 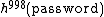 . Due to the one-way property of cryptographically secure hash functions, it is infeasible for the eavesdropper to reverse the hash function and obtain an earlier piece of the hash chain. In this example, the user could authenticate 1000 times before the hash chain were exhausted. Each time the hash value is different, and thus cannot be duplicated by an attacker.
. Due to the one-way property of cryptographically secure hash functions, it is infeasible for the eavesdropper to reverse the hash function and obtain an earlier piece of the hash chain. In this example, the user could authenticate 1000 times before the hash chain were exhausted. Each time the hash value is different, and thus cannot be duplicated by an attacker.
Binary hash chains
{{main article|Merkle tree}}Binary hash chains are commonly used in association with a hash tree. A binary hash chain takes two hash values as inputs, concatenates them and applies a hash function to the result, thereby producing a third hash value.
The above diagram shows a hash tree consisting of eight leaf nodes and the hash chain for the third leaf node. In addition to the hash values themselves the order of concatenation (right or left 1,0) or "order bits" are necessary to complete the hash chain.
Hash chain vs. blockchain
A hash chain is similar to a blockchain, as they both utilize a cryptographic hash function for creating a link between two nodes. However, a blockchain (as used by Bitcoin and related systems) is generally intended to support distributed consensus around a public ledger (data), and incorporates a set of rules for encapsulation of data and associated data permissions.
See also
- Challenge–response authentication
- Hash list – In contrast to the recursive structure of hash chains, the elements of a hash list are independent of each other.
- One-time password
- Key stretching
- Linked timestamping – Binary hash chains are a key component in linked timestamping.
- X.509
References
- Haydar Pasha, Nicosia
- Haydarpaşa-Gebze Commuter Line
- Haydarpaşa Railway Station
- Haydarpaşa suburban
- Haydar Safavi
- Haydar Saltık
- Hay Day
- Hay Day (mobile game)
- Haydee Coloso
- Haydee (given name)
- Haydee Politoff
- Haydee Santamaria
- Haydee Santamaria Cuadrado
- Haydee Santamaría
- Haydee Torres Beltran
- Hayden Barnes
- Hayden Barnes controversy
- Hayden Barnes Controversy
- Hayden Barns
- Hayden Byerly
- Hayden, Charles
- Hayden Cox
- Hayden Creek (Minnesota)
- Hayden Crozier
- Hayden Dunham