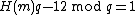- Equations
- Original Algorithm - insecure without hash function
- Secure and simplified Algorithm Remarks
- Security
- References
- External links
In cryptography the Rabin signature algorithm is a method of digital signature originally proposed by Michael O. Rabin in 1979. The Rabin signature algorithm was one of the first digital signature schemes proposed, and it is the only one to relate the hardness of forgery directly to the problem of integer factorization. The Rabin signature algorithm is existentially unforgeable in the random oracle model assuming the integer factorization problem is intractable. The Rabin signature algorithm is also closely related to the Rabin cryptosystem.
But, the RSA cryptosystem has a prominent role in the early days of public key cryptography, and the Rabin signature algorithm is not covered in most introductory courses on cryptography.
Equations
If H is a collision resistant hash function, m the message to sign and
and
the signature S is given by the equation
.
Everybody can verify
,
if the value 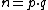 is public.
is public.
Original Algorithm - insecure without hash function
- Key Generation
- The signer S chooses primes p, q each of size approximately k/2 bits, and computes the product
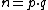 .
. - S then chooses a random b in
 .
. - The public key is (n, b).
- The private key is (p, q).
- The signer S chooses primes p, q each of size approximately k/2 bits, and computes the product
- Signing
- To sign a message m the signer S picks random padding U and calculates
 .
. - S then solves
 .
.
- To sign a message m the signer S picks random padding U and calculates
- If there is no solution S picks a new pad U and tries again.
- The signature on m is the pair (U, x)
- Verification
- Given a message m and a signature (U,x) the verifier V calculates x(x+b) mod n and
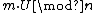 and verifies that they are equal.
and verifies that they are equal.
- Given a message m and a signature (U,x) the verifier V calculates x(x+b) mod n and
Secure and simplified Algorithm
The secure algorithm relies on a collision-resistant hash function  .
.
In most presentations the algorithm is simplified by choosing  . The hash function H with k output bits is assumed to be a random oracle and the algorithm works as follows:
. The hash function H with k output bits is assumed to be a random oracle and the algorithm works as follows:
- Key generation
- {{ordered list
|The signer S chooses primes p, q each of size approximately k/2 bits, and p, q mod 4 equals 3. He computes the product
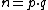 .
.|The public key is n.
|The private key is (p, q).
}}
- Signing
- {{ordered list
|To sign a message m the signer S picks random padding U and calculates H(m, U).
|If H(m, U) is not a square modulo n, S picks a new pad U.
|S computes one value x that solves the equation
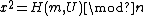 .
.|The signature on m is the pair (U, x).
}}
- Verification
- {{ordered list
|Given a message m and a signature (U, x), the verifier V calculates x2 mod n and H(m, U) and verifies that they are equal.
}}
Remarks
In some treatments the random pad U is eliminated. Instead we can eventually multiply the hash value with two numbers a or b with the properties 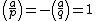 and
and 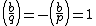 , where
, where  denotes the legendre symbol. Then for any H modulo n exactly one of the four numbers
denotes the legendre symbol. Then for any H modulo n exactly one of the four numbers  will be a square modulo n, and the signer chooses that one for his signature.
will be a square modulo n, and the signer chooses that one for his signature.
Even more simple, we change the message m until the signature can be verified.
def root(m, p, q):
while True: x = h(m) sig = pow(p,q-2,q) * p * pow(x,(q+1)/4,q) sig = ( pow(q,p-2,p) * q * pow(x,(p+1)/4,p) + sig ) % (nrabin) if (sig * sig) % nrabin == x: print "write extended message to file m " f = open('m','w') f.write(m) f.close() break m = m + ' ' return sigSecurity
If the hash function H is a random oracle, i.e. its output is truly random in 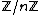 , then forging a signature on any message m is as hard as
, then forging a signature on any message m is as hard as
calculating the square root of a random element in 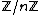 .
.
To prove that taking a random square root is as hard as factoring, we first note that in most cases there are four distinct square roots since n has two square roots modulo p and two square roots modulo q, and each pair gives a square root modulo n by the chinese remainder theorem. Some of the four roots may have the same value, but only with extreme low probability.
Now, if we can find two different square roots, x,y such that 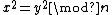 but
but  , then this immediately leads to a factorization of n since n divides
, then this immediately leads to a factorization of n since n divides 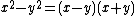 but it does not divide either factor. Thus taking
but it does not divide either factor. Thus taking 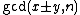 will lead to a nontrivial factorization of n.
will lead to a nontrivial factorization of n.
Now, we assume an efficient algorithm exists to find at least one square root. Then we pick a random r modulo n and square it 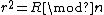 , then, using the algorithm we take one square root of R modulo n, we will get a new square root
, then, using the algorithm we take one square root of R modulo n, we will get a new square root 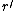 , and with probability half
, and with probability half  .
.
References
- Michele Elia, Davide Schipani, On the Rabin Signature, 2011 [https://www.math.uzh.ch/fileadmin/user/davide/publikation/SignatureRabin11.pdf PDF]
- Buchmann, Johannes. Einführung in die Kryptographie. Second Edition. Berlin: Springer, 2001. {{ISBN|3-540-41283-2}}
- Menezes, Alfred; van Oorschot, Paul C.; and Vanstone, Scott A. Handbook of Applied Cryptography. CRC Press, October 1996. {{ISBN|0-8493-8523-7}}
- Rabin, Michael. Digitalized Signatures and Public-Key Functions as Intractable as Factorization (in PDF). MIT Laboratory for Computer Science, January 1979.
- Scott Lindhurst, An analysis of Shank's algorithm for computing square roots in finite fields. in R Gupta and K S Williams, Proc 5th Conf Can Nr Theo Assoc, 1999, vol 19 CRM Proc & Lec Notes, AMS, Aug 1999.
- R Kumanduri and C Romero, Number Theory w/ Computer Applications, Alg 9.2.9, Prentice Hall, 1997. A probabilistic for square root of a quadratic residue modulo a prime.
External links
- Software Implementation with Python programming language
- Nutschau Monastery
- Nutschau Priory
- NUTS:CY
- NUTS:CZ
- NUTS:DE
- NUTS (disambiguation)
- NUTS:DK
- NUTS:EE
- Nut sert
- Nut-sert
- NUTS:ES
- NUTS:FI
- NUTS:FR
- NUTS:GR
- Nut shell
- Nut-shell
- Nutshell (band)
- Nutshell (Bury St Edmunds pub)
- Nutshell (Christian group)
- Nutshell (disambiguation)
- Nut shelled
- Nut-shelled
- Nutshelled
- Nut-sheller
- Nutsheller