- History
- Mathematical background
- Selected lattice-based cryptosystems Encryption schemes Signatures Hash functions Fully homomorphic encryption
- Security
- Functionality
- See also
- References
- Bibliography
Lattice-based cryptography is the generic term for constructions of cryptographic primitives that involve lattices, either in the construction itself or in the security proof. Lattice-based constructions are currently important candidates for post-quantum cryptography. Unlike more widely used and known public-key schemes such as the RSA, Diffie-Hellman or Elliptic-Curve cryptosystems, which are easily attacked by a quantum computer, some lattice-based constructions appear to be resistant to attack by both classical and quantum computers. Furthermore, many lattice-based constructions are known to be secure under the assumption that certain well-studied computational lattice problems cannot be solved efficiently.
History
In 1996, Miklós Ajtai introduced the first lattice-based cryptographic construction whose security could be based on the hardness of well-studied lattice problems.[1] Fundamentally, Ajtai's result was a worst-case to average-case reduction. I.e., he showed that a certain average-case lattice problem, known as Short Integer Solutions (SIS), is at least as hard to solve as a worst-case lattice problem. He then showed a cryptographic hash function whose security is equivalent to the computational hardness of SIS.
In 1998, Jeffrey Hoffstein (de), Jill Pipher, and Joseph H. Silverman introduced a lattice-based public-key encryption scheme, known as NTRU.[2] However, their scheme is not known to be at least as hard as solving a worst-case lattice problem.
The first lattice-based public-key encryption scheme whose security was proven under worst-case hardness assumptions was introduced by Oded Regev in 2005,[3] together with the Learning with Errors problem (LWE). Since then, much follow-up work has focused on improving Regev's security proof[4][5] and improving the efficiency of the original scheme.[6][7][7][8] Much more work has been devoted to constructing additional cryptographic primitives based on LWE and related problems. For example, in 2009, Craig Gentry introduced the first fully homomorphic encryption scheme, which was based on a lattice problem.[9]
Mathematical background
A lattice  is the set of all integer linear combinations of basis vectors
is the set of all integer linear combinations of basis vectors 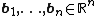 . I.e.,
. I.e.,

For example, 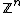 is a lattice, generated by the standard orthonormal basis for
is a lattice, generated by the standard orthonormal basis for  . Crucially, the basis for a lattice is not unique. For example, the vectors
. Crucially, the basis for a lattice is not unique. For example, the vectors  ,
, 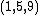 , and
, and  form an alternative basis for
form an alternative basis for 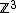 .
.
The most important lattice-based computational problem is the Shortest Vector Problem (SVP or sometimes GapSVP), which asks us to approximate the minimal Euclidean length of a non-zero lattice vector. This problem is thought to be hard to solve efficiently, even with approximation factors that are polynomial in  , and even with a quantum computer. Many (though not all) lattice-based cryptographic constructions are known to be secure if SVP is in fact hard in this regime.
, and even with a quantum computer. Many (though not all) lattice-based cryptographic constructions are known to be secure if SVP is in fact hard in this regime.
Selected lattice-based cryptosystems
Encryption schemes
- Peikert's Ring - Learning With Errors (Ring-LWE) Key Exchange[10]
- GGH encryption scheme
- NTRUEncrypt
Signatures
- Güneysu, Lyubashevsky, and Poppleman's Ring - Learning with Errors (Ring-LWE) Signature[11]
- GGH signature scheme
- NTRUSign
Hash functions
- SWIFFT
- LASH (Lattice Based Hash Function)[12][13]
Fully homomorphic encryption
{{See also|Fully homomorphic encryption}}- Gentry's original scheme.[9]
- Brakerski and Vaikuntanathan.[14][15]
Security
Lattice-based cryptographic constructions are the leading candidates for public-key post-quantum cryptography.[16] Indeed, the main alternative forms of public-key cryptography are schemes based on the hardness of factoring and related problems and schemes based on the hardness of the discrete logarithm and related problems. However, both factoring and the discrete logarithm are known to be solvable in polynomial time on a quantum computer.[17] Furthermore, algorithms for factorization tend to yield algorithms for discrete logarithm, and vice versa. This further motivates the study of constructions based on alternative assumptions, such as the hardness of lattice problems.
Many lattice-based cryptographic schemes are known to be secure assuming the worst-case hardness of certain lattice problems.[1][3][4] I.e., if there exists an algorithm that can efficiently break the cryptographic scheme with non-negligible probability, then there exists an efficient algorithm that solves a certain lattice problem on any input. In contrast, cryptographic schemes based on, e.g., factoring would be broken if factoring were hard "on an average input,'' even if factoring were in fact hard in the worst case. However, for the more efficient and practical lattice-based constructions (such as schemes based on NTRU and even schemes based on LWE with more aggressive parameters), such worst-case hardness results are not known. For some schemes, worst-case hardness results are known only for certain structured lattices[6] or not at all.
Functionality
For many cryptographic primitives, the only known constructions are based on lattices or closely related objects. These primitives include fully homomorphic encryption,[9] indistinguishability obfuscation,[18] cryptographic multilinear maps, and functional encryption.[18]
See also
- Lattice problems
- Learning with errors
- Post-quantum cryptography
- Ring learning with errors
- Ring learning with Errors Key Exchange
References
2. ^{{Cite book|last=Hoffstein|first=Jeffrey|last2=Pipher|first2=Jill|last3=Silverman|first3=Joseph H.|date=1998-06-21|title=NTRU: A ring-based public key cryptosystem|journal=Algorithmic Number Theory|volume=1423|language=en|pages=267–288|doi=10.1007/bfb0054868|series=Lecture Notes in Computer Science|isbn=978-3-540-64657-0|citeseerx=10.1.1.25.8422}}
3. ^1 {{Cite book|last=Regev|first=Oded|date=2005-01-01|title=On Lattices, Learning with Errors, Random Linear Codes, and Cryptography|journal=Proceedings of the Thirty-seventh Annual ACM Symposium on Theory of Computing|series=STOC '05|location=New York, NY, USA|publisher=ACM|pages=84–93|doi=10.1145/1060590.1060603|isbn=978-1581139600|citeseerx=10.1.1.110.4776}}
4. ^1 {{Cite book|last=Peikert|first=Chris|date=2009-01-01|title=Public-key Cryptosystems from the Worst-case Shortest Vector Problem: Extended Abstract|journal=Proceedings of the Forty-first Annual ACM Symposium on Theory of Computing|series=STOC '09|location=New York, NY, USA|publisher=ACM|pages=333–342|doi=10.1145/1536414.1536461|isbn=9781605585062|citeseerx=10.1.1.168.270}}
5. ^{{Cite book|last=Brakerski|first=Zvika|last2=Langlois|first2=Adeline|last3=Peikert|first3=Chris|last4=Regev|first4=Oded|last5=Stehlé|first5=Damien|date=2013-01-01|title=Classical Hardness of Learning with Errors|journal=Proceedings of the Forty-fifth Annual ACM Symposium on Theory of Computing|series=STOC '13|location=New York, NY, USA|publisher=ACM|pages=575–584|doi=10.1145/2488608.2488680|isbn=9781450320290|arxiv=1306.0281}}
6. ^1 {{Cite book|last=Lyubashevsky|first=Vadim|last2=Peikert|first2=Chris|last3=Regev|first3=Oded|date=2010-05-30|title=On Ideal Lattices and Learning with Errors over Rings|journal=Advances in Cryptology – EUROCRYPT 2010|volume=6110|language=en|pages=1–23|doi=10.1007/978-3-642-13190-5_1|series=Lecture Notes in Computer Science|isbn=978-3-642-13189-9|citeseerx=10.1.1.352.8218}}
7. ^{{Cite journal|last=Alkim|first=Erdem|last2=Ducas|first2=Léo|last3=Pöppelmann|first3=Thomas|last4=Schwabe|first4=Peter|date=2015-01-01|title=Post-quantum key exchange - a new hope|url=http://eprint.iacr.org/2015/1092}}
8. ^{{Cite journal|last=Bos|first=Joppe|last2=Costello|first2=Craig|last3=Ducas|first3=Léo|last4=Mironov|first4=Ilya|last5=Naehrig|first5=Michael|last6=Nikolaenko|first6=Valeria|last7=Raghunathan|first7=Ananth|last8=Stebila|first8=Douglas|date=2016-01-01|title=Frodo: Take off the ring! Practical, Quantum-Secure Key Exchange from LWE|url=http://eprint.iacr.org/2016/659}}
9. ^1 2 {{Cite thesis|last=Gentry|first=Craig|title=A Fully Homomorphic Encryption Scheme|date=2009-01-01|publisher=Stanford University|url=http://dl.acm.org/citation.cfm?id=1834954|place=Stanford, CA, USA}}
10. ^1 {{cite web| url=https://eprint.iacr.org/2014/070.pdf| title=Lattice Cryptography for the Internet| last=Peikert| first=Chris| date=2014-07-16| publisher=IACR| accessdate=2017-01-11}}
11. ^{{cite paper| chapter-url=https://www.iacr.org/archive/ches2012/74280529/74280529.pdf| first1=Tim| title=Cryptographic Hardware and Embedded Systems – CHES 2012| volume=7428| pages=530–547| last1=Güneysu| first2=Vadim| last2=Lyubashevsky| first3=Thomas| last3=Pöppelmann| publisher=IACR| doi=10.1007/978-3-642-33027-8_31| accessdate=2017-01-11| year=2012| series=Lecture Notes in Computer Science| isbn=978-3-642-33026-1| chapter=Practical Lattice-Based Cryptography: A Signature Scheme for Embedded Systems}}
12. ^{{cite web|url=http://www.cs.bris.ac.uk/~page/research/lash.html |title=LASH: A Lattice Based Hash Function |accessdate=2008-07-31 |deadurl=bot: unknown |archiveurl=https://web.archive.org/web/20081016235719/http://www.cs.bris.ac.uk/~page/research/lash.html |archivedate=October 16, 2008 |df= }} (broken)
13. ^{{cite paper| chapter-url=https://eprint.iacr.org/2007/430.pdf| authors=Scott Contini, Krystian Matusiewicz, Josef Pieprzyk, Ron Steinfeld, Jian Guo, San Ling and Huaxiong Wang| title=Fast Software Encryption| volume=5086| pages=207–223| year=2008| doi=10.1007/978-3-540-71039-4_13| series=Lecture Notes in Computer Science| isbn=978-3-540-71038-7| chapter=Cryptanalysis of LASH}}
14. ^{{Cite journal|last=Brakerski|first=Zvika|last2=Vaikuntanathan|first2=Vinod|date=2011|title=Efficient Fully Homomorphic Encryption from (Standard) LWE|url=https://eprint.iacr.org/2011/344}}
15. ^{{Cite journal|last=Brakerski|first=Zvika|last2=Vaikuntanathan|first2=Vinod|date=2013|title=Lattice-Based FHE as Secure as PKE|url=https://eprint.iacr.org/2013/541}}
16. ^{{cite paper|title=Lattice-based cryptography|first1=Daniele|last1=Micciancio|first2=Oded|last2=Regev|date=2008-07-22|url=https://www.cims.nyu.edu/~regev/papers/pqc.pdf|accessdate=2017-01-11}}
17. ^{{Cite journal|last=Shor|first=Peter W.|date=1997-10-01|title=Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer|journal=SIAM Journal on Computing|volume=26|issue=5|pages=1484–1509|doi=10.1137/S0097539795293172|issn=0097-5397|arxiv=quant-ph/9508027}}
18. ^1 {{Cite journal|last=Garg|first=Sanjam|last2=Gentry|first2=Craig|last3=Halevi|first3=Shai|last4=Raykova|first4=Mariana|last5=Sahai|first5=Amit|last6=Waters|first6=Brent|date=2013-01-01|title=Candidate Indistinguishability Obfuscation and Functional Encryption for all circuits|url=https://eprint.iacr.org/2013/451}}
Bibliography
- Oded Goldreich, Shafi Goldwasser, and Shai Halevi. "Public-key cryptosystems from lattice reduction problems". In CRYPTO ’97: Proceedings of the 17th Annual International Cryptology Conference on Advances in Cryptology, pages 112–131, London, UK, 1997. Springer-Verlag.
- Phong Q. Nguyen. "Cryptanalysis of the Goldreich–Goldwasser–Halevi cryptosystem from crypto ’97". In CRYPTO ’99: Proceedings of the 19th Annual International Cryptology Conference on Advances in Cryptology, pages 288–304, London, UK, 1999. Springer-Verlag.
- Chris Peikert, “Public-key cryptosystems from the worst-case shortest vector problem: extended abstract,” in Proceedings of the 41st annual ACM symposium on Theory of computing (Bethesda, MD, USA: ACM, 2009), 333–342, DOI 10.1145/1536414.1536461
- Oded Regev. Lattice-based cryptography. In Advances in cryptology (CRYPTO), pages 131–141, 2006.
- Ringedalsvatnet
- Ringed antpipit
- Ringed dosinia
- Ringed hornsnail
- Ringed kingfisher
- Ringed map turtle
- Ringed salamander
- Ringed Sawback
- Ringed sideroblast
- Ringed-snake
- Ringed Storm-petrel
- Ringed Storm-Petrel
- Ringed Storm Petrel
- Ringed warbling finch
- Ringed Warbling-Finch
- Ringed woodpecker
- Ringe, Germany
- Ringelai
- Ringelberg
- Ringelbergius
- Ringel-Kotzig conjecture
- Ringelnatz
- Ringelsdorf-Niederabsdorf
- Ringel–Youngs theorem
- Ring endomorphism