- Description
- Security properties
- References
- External links
The YAK is a public-key authenticated key agreement protocol, proposed by Feng Hao in 2010.[1] It is considered the simplest among the related protocols, including MQV, HMQV, Station-to-Station protocol, SSL/TLS etc. The authentication is based on public key pairs. As with other protocols, YAK normally requires a Public Key Infrastructure to distribute authentic public keys to the communicating parties.
Description
Two parties, Alice and Bob, agree on a group 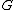 with generator
with generator  of prime order
of prime order  in which the discrete log problem is hard. Typically a Schnorr group is used. In general, YAK can use any prime order group that is suitable for public key cryptography, including elliptic curve cryptography. Let
in which the discrete log problem is hard. Typically a Schnorr group is used. In general, YAK can use any prime order group that is suitable for public key cryptography, including elliptic curve cryptography. Let 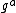 be Alice's long-term public key and
be Alice's long-term public key and 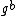 be Bob's. The protocol executes in one round:
be Bob's. The protocol executes in one round:
Alice selects 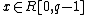 and sends out
and sends out 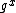 together with a zero-knowledge proof (using for example Schnorr non-interactive zero-knowledge proof as described in RFC 8235) for the proof of the exponent
together with a zero-knowledge proof (using for example Schnorr non-interactive zero-knowledge proof as described in RFC 8235) for the proof of the exponent  . Similarly, Bob selects
. Similarly, Bob selects 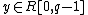 and sends out
and sends out 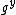 together with a zero-knowledge proof for the proof of the exponent
together with a zero-knowledge proof for the proof of the exponent  . Here, the notation
. Here, the notation 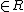 denotes an element selected randomly with uniform probability.
denotes an element selected randomly with uniform probability.
The above communication can be completed in one round as neither party depends on the other. When it finishes, Alice and Bob verify the received zero-knowledge proofs. Alice then computes 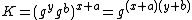 . Similarly, Bob computes
. Similarly, Bob computes  . With the same keying material
. With the same keying material  , Alice and Bob can derive a session key using a cryptographic hash function:
, Alice and Bob can derive a session key using a cryptographic hash function: 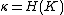 .
.
Security properties
The use of well-established zero-knowledge proof primitives such as Schnorr's scheme greatly simplifies the security proofs. Given that the underlying zero knowledge proof primitive is secure, the YAK protocol is proved to fulfill the following properties.
- Private key security – An attacker cannot learn the user's static private key even if he is able to learn all session-specific secrets in any compromised session.
- Full forward secrecy – Session keys that were securely established in the past uncorrupted sessions will remain incomputable in the future even when both users' static private keys are disclosed.
- Session key security – An attacker cannot compute the session key if he impersonates a user but has no access to the user's private key.
References
External links
- On Robust Key Agreement Based on Public Key Authentication (Full Paper)
- Filippo Grandi
- Filippo Gurrieri
- Filipp Oktyabrskiy
- Filip Polasek
- Filip Polc
- Filippo Lombardi (footballer)
- Filip Polášek
- Filippo Mancini
- Filippo Mannucci
- Filippo Messori
- Filippo Negroli
- Filippo neri
- Filippo Paulucci
- Filippo Perlo
- Filippo Perucchini
- Filippo "Philip" De Grassi
- Filippo Porcari
- Filipportera
- Filippo Sabetti
- Filippo Savini
- Filippo Scardina
- Filippo Soffici
- Filippos Petsalnikos
- Filippo Spinola, 2nd Marquis of Los Balbases
- Filippo Spinola, 2nd Marquis of the Balbases