- Structure of algorithm Basic structure Structure of basic functions Key schedule Encryption Decryption
- Modes of operation
- Cryptoanalysis
- See also
- References
| name = M8
| designers = Hitachi
| date of registration = 19 March 1999
| derived from = M6
| derived to =
| related to =
| key size =64 bits
| input size =
| output size =
| structure = Feistel network
| round number =
| cryptanalysis =
}}
In cryptography, M8 is a block cipher designed by Hitachi in 1999. The algorithm negotiates introduced in 1997 M6, with the modified key length, which is enlarged to 64 bits or more. This cipher operates with Feistel network and designed to reach high performance on small implementation or 32 bits devices. For instance, by using round numbers = 10 it present encryption speed at 32 Mbps for dedicated hardware of 6K gates and 25 MHz clock or 208 Mbps for program, that uses C-language and Pentium-I 266MHz. Due to the openness of description, it should not be used in open or multivendor software.
Structure of algorithm
Basic structure
The structural characteristics are that the cipher is based on substitution-permutation block like DES. There are 3 kinds of calculations: 32-bit circular rotation, addition in modulus 232 and 32 bits-wise XOR. Actual function may be different each round. Key is used to be calculated using its value and that defines actual function each round.
After decision process, which is using round number, decision and expansion keys, the algorithm gets basic function (e π) or (d π). Then it is used either by key scheduler (which also takes 256 key expansion key and 64 bits data key), that products 256 bits execution key, and encryption/decryption block.
Algorithm decision key is consist of 24 bits. First 9 bits determine calculations: 0 means addition in 232modulus, 1 means bit-wise XOR. Other 3 blocks for 5 bits define left circular rotations. Algorithm expansion key concludes 3 blocks for 32bits, which determine α,β and γ.
The difference between basic function is only in the order of permutations: (e π) does it in the end, (d π) - at the beginning of calculation block.
Structure of basic functions
The structure has 9 blocks of calculations and 3 optionally blocks of left circle rotations.
It has a 64-bit block size and also 64-bit key length. It's Feistel cipher with S-blocks, that are dependent on large execution key.
At the start, there is permutation for (d π). Then algorithm takes the first block of plaintext and makes calculation 1 using KL, then it optionally does rotation and goes to calculation 2. The it repeats, but there is α instead of KL. Then it uses β for doing cal. 5. Then algorithm does calculations and rotation, described earlier, but using KR. Further, it is used γ to do calc.8 and obtained result calculates with the other block of plaintext. In conclusion, algorithm permutates blocks.
For the (e π) it's the same, excluding the order of permutation and calculations of blocks.
Key schedule
The execution key obtains from 256-bit key expansion key, which divides into 2 identical set of four 64-bit blocks K0–K3, and 64 bit of data key. Every block of key expansion key is used to calculate with 32 bit of data key by (e Π [0-7]) and gives eight 32-bit blocks of expansion key on the output.
Encryption
Obtained expansion key divides into 4 pair block of 32-bit. This block divides into 32 bits of left and right range it is used to do calculations with 64-bit plaintext blocks using 4 subsequent steps. Then obtained ciphertext encrypts again using the same pairs of block of expansion key and the same steps round times.
Decryption
To decrypt cipher text it is enough to do the same operation, but using the another basic function.
Modes of operation
As determined in ISO 8372 or ISO/IEC 101116 there are 4 applicable modes:
- Electronic Codebook (ECB) mode
- The simplest encryption mode. Using this plaintext divides into blocks, which encrypts separately. The disadvantage of this method is the lack of diffusion. It means that data hides not enough well and it's not recommended to use for cryptographic protocols at all.
- Cipher Block Chaining (CBC) mode
- In this mode each block of plaintext is XORed with the previous before being encrypted. Every block will depend on all previous blocks and it should be used initialization vector in the first block to make each message unique.
- Cipher Feedback (CFB) mode
- This mode mode, a close relative of CBC, makes a block cipher into a self-synchronizing stream cipher. Operation is very similar; in particular, CFB decryption is almost identical to CBC encryption performed in reverse.
- Output Feedback (OFB) mode
- This mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption.
Because of the symmetry of the XOR operation, encryption and decryption are exactly the same.
- This mode makes a block cipher into a synchronous stream cipher. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. Just as with other stream ciphers, flipping a bit in the ciphertext produces a flipped bit in the plaintext at the same location. This property allows many error correcting codes to function normally even when applied before encryption.
Cryptoanalysis
- In M8 key determines both calculation objects and round numbers. If a hostile person knows the structure of every round, it will be possible to evaluate M8 by using conventional methods. With the estimate of Hitachi, there is possibility that if it has less than 10 rounds, it will be easier to encrypt M8 than DES. Therefore it's recommended to use >10 rounds. The cryptographic strength increases as the number of rounds are growing, but it's necessary to remember, that the speed of encryption will decrease inversely as round numbers. If the structure of rounds are not known, there is only the way to do exhaustive search, which will be non-effective due to a huge number of round function variations. Summary, it's need to trade-off between speed and safety of the algorithm.
- Like an M6, it's sensitive to mod n cryptanalysis, which was suggested in 1999 by John Kelsey, Bruce Schneier, and David Wagner. It is a form of partitioning cryptanalysis that exploits unevenness in how the cipher operates over equivalence classes (congruence classes) modulo n. These attacks used the properties of binary addition and bit rotation modulo a Fermat prime. One known plaintext allows recovering the key with about 235 trial encryptions; "a few dozen" known plaintexts reduces this to about 231.
- Because it has weak key schedule, M8 is subject to decryption to a slide attack, which requires less known plaintext than mod n cryptanalysis, but less calculations. Lets assume that cipher has n bits and uses key scheduler, which consist K1-KM as keys of any length. This encryption method breaks up into identical permutation functions F of cipher. This functions may consist of more than 1 round of chiper, it is defined by key-shedule. For example, if cipher uses alternating key-schedule, which switches between K1 and K2, there are 2 rounds into F. Every Ki will appear at least once.
Depending of characteristics of cipher, next step will collect 2n/2 pairs of plaintext and ciphertext. By the birthday paradox, it should not be required to collect more than this number. Theh these pairs, which are denoted as (P,C), are used to find "slid" pairs, which are denoted as (P0,C0)(P1,C1). Every "slid" pair has the property P0=F(P1) and C0=F(C1). "Slid" pair get its name because it "slid" over one encryption. It can be imagined like result of applying one time function F.
Once this pair is identified, the key can be easily extracted from this pairing, and the cipher is broken because of vulnerability to known-plaintext attacks.
The process of finding a slid pair can be different but follows the same basic scheme.One uses the fact that it is relatively easy to extract the key from just one iteration of F. Choose any pair ofplaintext-ciphertext pairs, and check to see what the keys corresponding to
and check to see what the keys corresponding to  and
and 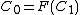 are. If these keys match, this is a slid pair; otherwise move on to the next pair.
are. If these keys match, this is a slid pair; otherwise move on to the next pair.
With plaintext-ciphertext one slid pair is expected. The number of false-positives depends on structure of the algorithm. False-positives can be reduced by applying keys to different message-cipherkey pair, because it's very low possibility for a good cipher, that the wrong key can correctly encypt >2 messages.
plaintext-ciphertext one slid pair is expected. The number of false-positives depends on structure of the algorithm. False-positives can be reduced by applying keys to different message-cipherkey pair, because it's very low possibility for a good cipher, that the wrong key can correctly encypt >2 messages.
Sometimes the structure of the cipher greatly reduces the number of plaintext-ciphertext pairs needed, and thus also a large amount of the work.
The clearest of these examples is the Feistel cipher using a cyclic key schedule.The reason for this is given a the search is for a
the search is for a  . This reduces the possible paired messages from
. This reduces the possible paired messages from  down to
down to  (since half the message is fixed) and so at most
(since half the message is fixed) and so at most 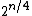 plaintext-ciphertext pairs are needed in order to find a slid pair.
plaintext-ciphertext pairs are needed in order to find a slid pair.
See also
- M6 (cipher)
- Data Encryption Standard
- Slide attack
- Mod n cryptanalysis
References
- {{cite web
|url=http://www.chrismitchell.net/ISO-register/0020.pdf
|title=ISO/IEC9979-0020 Register Entry
|publisher=ISO/IEC 9979 Register of Cryptographic Algorithms
|website=Professor Chris Mitchell, Information Security Group, Royal Holloway, University of London
}}
- {{cite web
|url=https://www.schneier.com/academic/paperfiles/paper-mod3.pdf
|title=Mod n Cryptanalysis, with Applications Against RC5P and M6
|publisher=Fast Software Encryption, Sixth International Workshop Proceedings (March 1999), Springer-Verlag, 1999, pp. 139-155.
|website=J. Kelsey, B. Schneier, and D. Wagner
}}
- {{cite journal
|author1=E.K. Grossman |author2=B. Tuckerman
|lastauthoramp=yes | title = Analysis of a Feistel-like cipher weakened by having no rotating key
| publisher = IBM Thomas J. Watson Research Report RC 6375
| year = 1977 }}
- {{cite book
|author1=Henry Beker |author2=Fred Piper
|lastauthoramp=yes | title = Cipher Systems: The Protection of Communications
| publisher = John Wiley & Sons
| year = 1982
| pages = 263–267
| isbn = 0-471-89192-4 }} (contains a summary of the paper by Grossman and Tuckerman)
- {{cite conference
| author = Alex Biryukov and David Wagner
| title = Slide Attacks
| conference = 6th International Workshop on Fast Software Encryption (FSE '99)
| pages = 245–259
| publisher = Springer-Verlag
| date = March 1999
| location = Rome
| url = http://www.cs.berkeley.edu/~daw/papers/slide-fse99.ps
| format = PDF/PostScript
| accessdate = 2007-09-03 }}
- {{cite conference
|author1=Alex Biryukov |author2=David Wagner
|lastauthoramp=yes | title = Advanced Slide Attacks
| conference = Advances in Cryptology, Proceedings of EUROCRYPT 2000
| pages = 589–606
| publisher = Springer-Verlag
| date = May 2000
| location = Bruges
| url = https://www.iacr.org/archive/eurocrypt2000/1807/18070595-new.pdf
| format = PDF/PostScript
| accessdate = 2007-09-03 }}
- {{cite conference
| author = S. Furuya
| title = Slide Attacks with a Known-Plaintext Cryptanalysis
| conference = 4th International Conference on Information Security and Cryptology (ICISC 2001)
| pages = 214–225
| publisher = Springer-Verlag
| date = December 2001
| location = Seoul
| url = http://register.itfind.or.kr/Report01/200401/IITA/IITA-0763-017/IITA-0763-017.pdf
| format = PDF
| accessdate = 2007-09-03 }}
- {{cite journal
| author = Eli Biham
| title = New Types of Cryptanalytic Attacks Using Related Keys
| journal = Journal of Cryptology
| volume = 7
| issue = 4
| issn = 0933-2790
| pages = pp. 229–246
| year = 1994
| url = http://citeseer.ist.psu.edu/biham94new.html
| format = PDF/PostScript
| accessdate = 2007-09-03
| doi=10.1007/bf00203965}}
- {{cite journal
| author = M. Ciet, G. Piret, J. Quisquater
| title = Related-Key and Slide Attacks: Analysis, Connections, and Improvements
| year = 2002
| url = http://citeseer.ist.psu.edu/560898.html
| format = PDF/PostScript
| accessdate = 2007-09-04 }}{{Hitachi}}{{Cryptography navbox | block}}{{crypto-stub}}
- Ben Guild
- Ben Guillory
- Ben Guiney
- Ben Guintini
- Ben Gulak
- Ben Gulliver
- Ben Gunn (disambiguation)
- Ben Gunn (Treasure Island)
- Bengur bryan
- Bengur Bryan
- Bengur bryan & co
- Bengur bryan & co.
- Bengur Bryan & Co., Inc.
- Ben Gurion High School
- Ben-Gurion House
- Ben Gurion House
- Ben-Gurion International Airport Garden
- Ben Gurion National Solar Energy Center
- Ben-Gurion National Solar Energy Center
- Ben Gurion university
- Bengut River
- Benguț River
- Bengy-sur-Craon
- Ben Gördüm
- Bengü